Modus Operandi
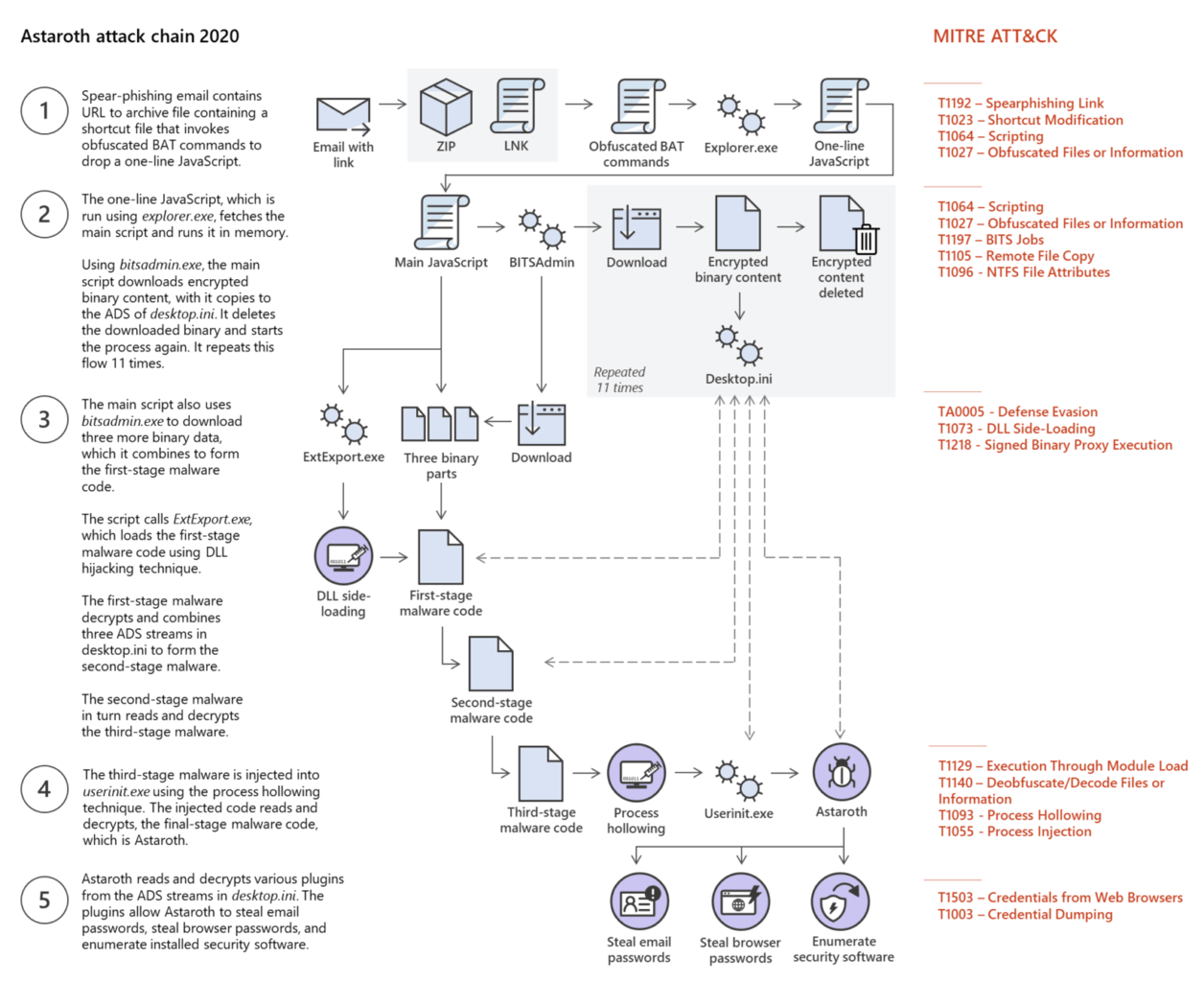
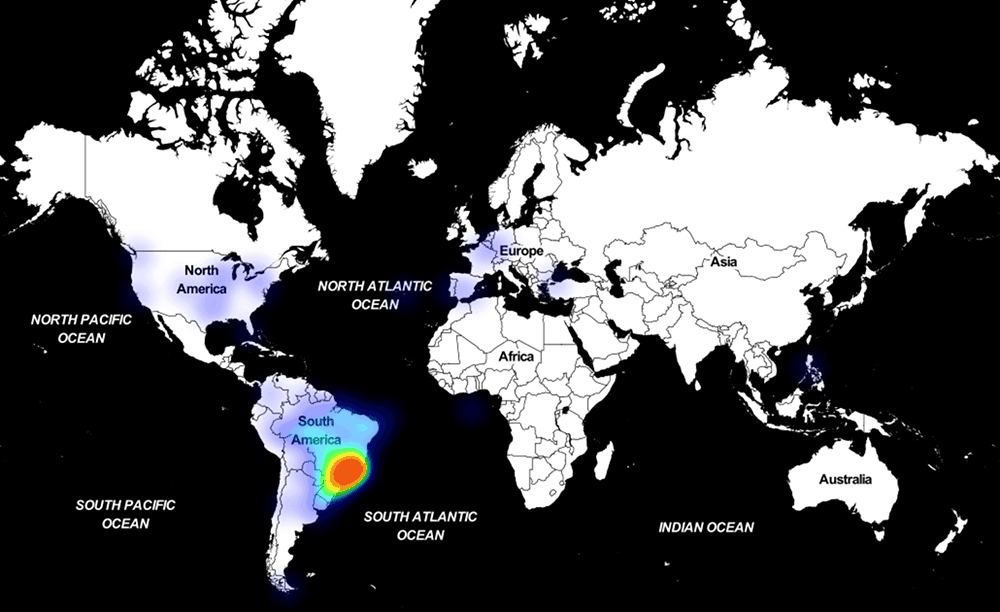
Astaroth’s methods of exploiting are different, but not the initial infection. This malware group starts with a phishing email, where it lures the potential victims to click on a link that redirects them to a website hosting a file as.LNK. This would attach the attacker’s payload and retrieved into the host system stealthily by exploiting Alternate Data Streams (ADS)! This file attribute allows an attacker to attach data to an existing file. As explained by Hardik Suri, a member of Microsoft’s Defender ATP research team, after victims clicking on.LNK in the redirected website, it runs an obfuscated BAT line that dumps a JavaScript file into Pictures folder and commands explorer.exe to run the payload retrieved. This was successful by exploiting the Alternate Data Streams (ADS) for remaining in stealth. Further, it exploits ExtExport.exe for loading the Payload. Abusing these options is legitimate, thus antivirus software won’t flag as suspicious activity. This privilege lets them decrypt two plug-ins as NirSoft MailPassView and NirSoft WebBrowserPassView tool. The former one is for obtaining email client passwords and the latter ones for retrieving passwords from browsers. Another abusing is done to BITSAdmin, which is used for downloading the encrypted dump from the attacker’s C&C server. If not, this was actually used by system admins for downloading or uploading jobs and monitor their progress. The initial email file statement that asks for clicking on the link would look like this, “Please find in the link below the STATEMENT #56704/2019 AND LEGAL DECISION, for due purposes”, that would take you to.LNK file for further dumping payload. Microsoft warned the community about this and said Brazil is being targeted vastly. Source: Microsoft