Using AWS and Oracle Cloud
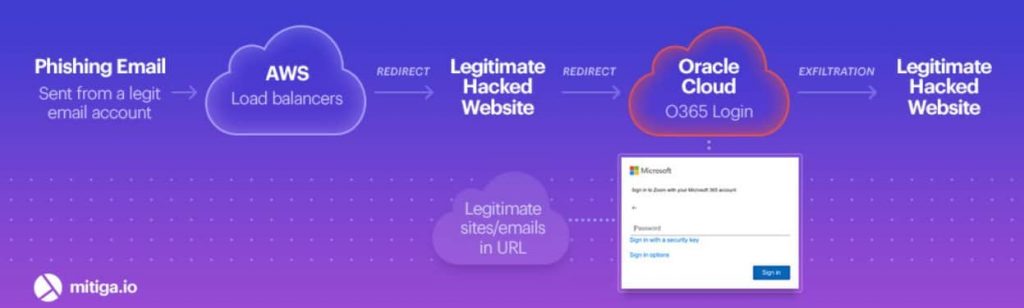
Researchers at v, a cybersecurity firm said that C-level executives at small and medium-sized businesses and financial institutions from Australia and the US are targeted in this campaign. They start with a simple luring tactic of inviting the target to a Zoom meeting or other voice message notifications from a boss, eventually redirecting them to a fake site when clicked on links in the mail. Researchers said the redirection flow is what made hackers special here, as they used authentic services to gain belief. The target will be redirected to a fake phishing website that’s already compromised. Here, they’ll be asked to log in using their Microsoft Office 365 credentials, which will be transferred instantly to the hacker’s C2 once entered. It should be noted that the spam emails were sent using compromised email accounts. Researchers have discovered over 40 such compromised websites in this campaign. Also, some HTML code snippets in the phishing pages gave hint at it to be a phishing-as-a-service business! These could be rented to other cybercriminals for obtaining credentials for other malicious purposes. Thus, to avoid such attacks, researchers have suggested using 2FA protocols for better account security. Also, to remain vigilant about the unknown incoming emails and URLs they’re carrying within.