Clast82 – A New Android Malware Dropper
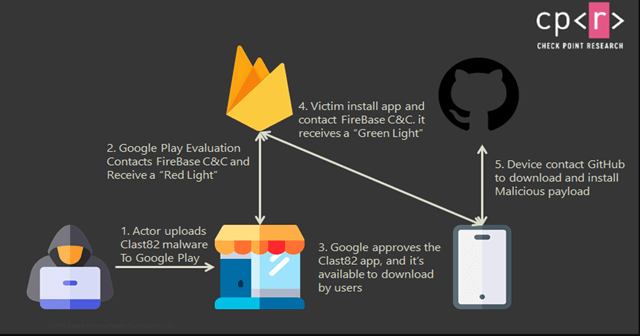
Hackers in their modus operandi deploy several techniques to avoid detection. This could be the use of legitimate software, social engineering, etc. A new malware campaign detected by researchers at Check Point, a cybersecurity firm has been using one of these techniques to stay unsuspicious, and infect Android devices for stealing data. As per the report, several apps found in Google Playstore are having a malware dropper named Clast82, which was clean when installed and isn’t flagged suspicious by Google while listing. But after being installed in the device, the dropper connects to the hacker’s C2 via Firebase for instructions. These are to learn from where it has to procure the malicious payload from. It’s reported that the hacker has set over 100 payload paths to direct his dropper. All from GitHub! This is interesting since payloads procured from legitimate paths like GitHub won’t raise any flags by the antivirus software, thus smoothening the flow. The malicious payload brought in is the AlienBot Banker and MRAT. AlienBot is a banking trojan infecting devices and gives powers remote handling the device to authors. The ultimate goal of AlienBot is to steal the banking credentials and 2FA codes of the target. Researchers spotted this suspicious activity after finding the email addresses and GitHub accounts set in those apps in Google Playstore belonging to one. The maker of this dropper has tweaked the spreading apps in such a way to softly comply with Google’s Playstore rules, and also perform his malicious work. For example, for a rule to show a notification at the top, these apps name the foreground process running in their apps like Google Play services. Also, they ask for reinstalling the app from unknown sources and would force users to allow them frequent notifications. Apps carrying this dropper were found to be Cake VPN, Pacific VPN, eVPN, BeatPlayer, QR/Barcode Scanner MAX, Music Player, tooltipnatorlibrary, and QRecorder. After the initial discovery on January 27th, Google has removed the concerned apps from the Playstore on February 9th.