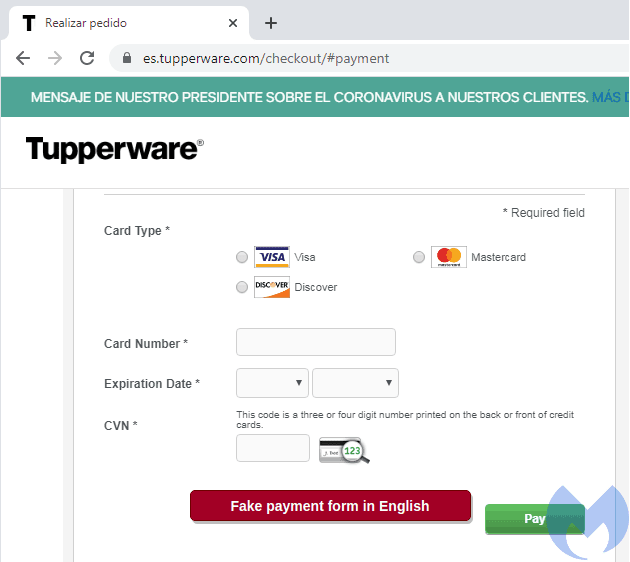
Unseen Payment Page
Malwarebytes, an American CyberSecurity firm that unearthed this fact claims to have contacted Tupperware in all the ways possible but didn’t receive any reply. In the story published, it cracked how fraudsters successfully planted their skimming code in the payment gateway page. This could’ve affected thousands of shoppers already, considering the volume Tupperware receives monthly. It’s ranked below 100,000 in Alexa ranking and has over a million hits per month. Aside from potential data hack, adversaries could be using general Magecart scripts for scraping the details out. This was explained by Malwarebytes as, “a suspicious-looking iframe loaded from deskofhelp[.]com when visiting the checkout page at tupperware[.]com. This iframe is responsible for displaying the payment form fields presented to online shoppers.” This fake payment page could have details of credit cards and send them to hacker’s remote servers.
Facts from Inspection
Further analysis into this revealed the suspicious site – deskofhelp[.]com was created on 9th March with a Russian email as [email protected][.]ru. It’s first found when there’s a suspicious PNG image file on the homepage, and the source code confirming its suspicion. Moreover, a cross-check as localized payment gateway showing still in English, further confirmed the malicious incident. After all, the sensitive details in question are the entered credit card’s number, CVV code, expiry date, first and last name, phone number, and billing address. The team said they don’t know how the site was compromised, but tried alerting it for stopping further exploitation. As the breakout of COVID-19 pandemic led many to restrict to homes and order things online much, which could cause more thefts. Source: Malwarebytes