They’re found to be gaining the admin account access initially and then altering the site”s index files and later the XML files to abuse the site’s search rankings as well.
A New Wave of Attacks on Weak WordPress Sites
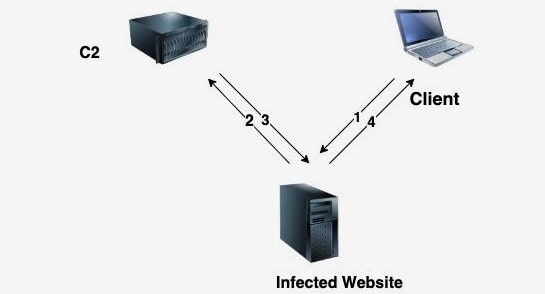
Attacks on WordPress sites are pretty common these days. The latest campaign spotted by Larry Cashdollar, a security researcher for the Akamai security team, may set a new trend if seen garnering desired results. According to his report, a new malware group is actively targeting weak WordPress sites. This was caught using his honeypot made for learning such attacks. He detailed that the malware gang is brute-force attacking WordPress sites with weak credentials for gaining admin access. After this, they’re overwriting the site’s index file and adding their malicious code to it.
This was intended for redirecting the site’s genuine traffic to the hacker’s C2, where the actual malicious activity happens. As the researcher described, the eligible visitor will be shown an e-commerce website containing all common objects for purchase. He said that about 7,000 such online stores were hosted by the hackers while being connected to his honeypot. They were also reportedly manipulating the site’s XML files to include their e-commerce stores alongside the site’s pages and submitting them to Google for better reach. While this helps hackers reach new victims, it significantly degrades the site’s SERP ranking in search results because of mixed and unrelated keywords. This can give rise to a new type of attack like SEO extortion, where hackers can manipulate the site’s value in search results and demand them ransom for reverting its position. Thus, safeguarding from such attacks is possible only through setting strong passwords and patching any known vulnerabilities in your site.